Automated Certificate Management
TSB supports automated certificate management for TSB components. You can enable TSB to provision a self signed root CA that will be used to issue TSB certificates such as TLS certificates for TSB front-envoy TLS certificate, internal certificates for communication between control plane to management plane and intermediate CA certificates for application clusters that will be used by Istio in the cluster to issue certificates for application workloads.
TSB's automated certificate management currently has following limitations:
- Does not support using external root CA. Currently it only supports self signed root CA. See Using External Certificate Management if you want to use existing PKI.
- Does not support configuring certificate rotation period. This is currently fixed to 90 days for TSB TLS and internal certificates and 1 year for cluster intermediate CA certificates.
Automated certificate management currently only works when you enable Isolation boundary. Make sure to enable isolation boundary from the start to avoid istiod provision self signed intermediate CA.
PKI pattern when using automated certificate management is shown below:
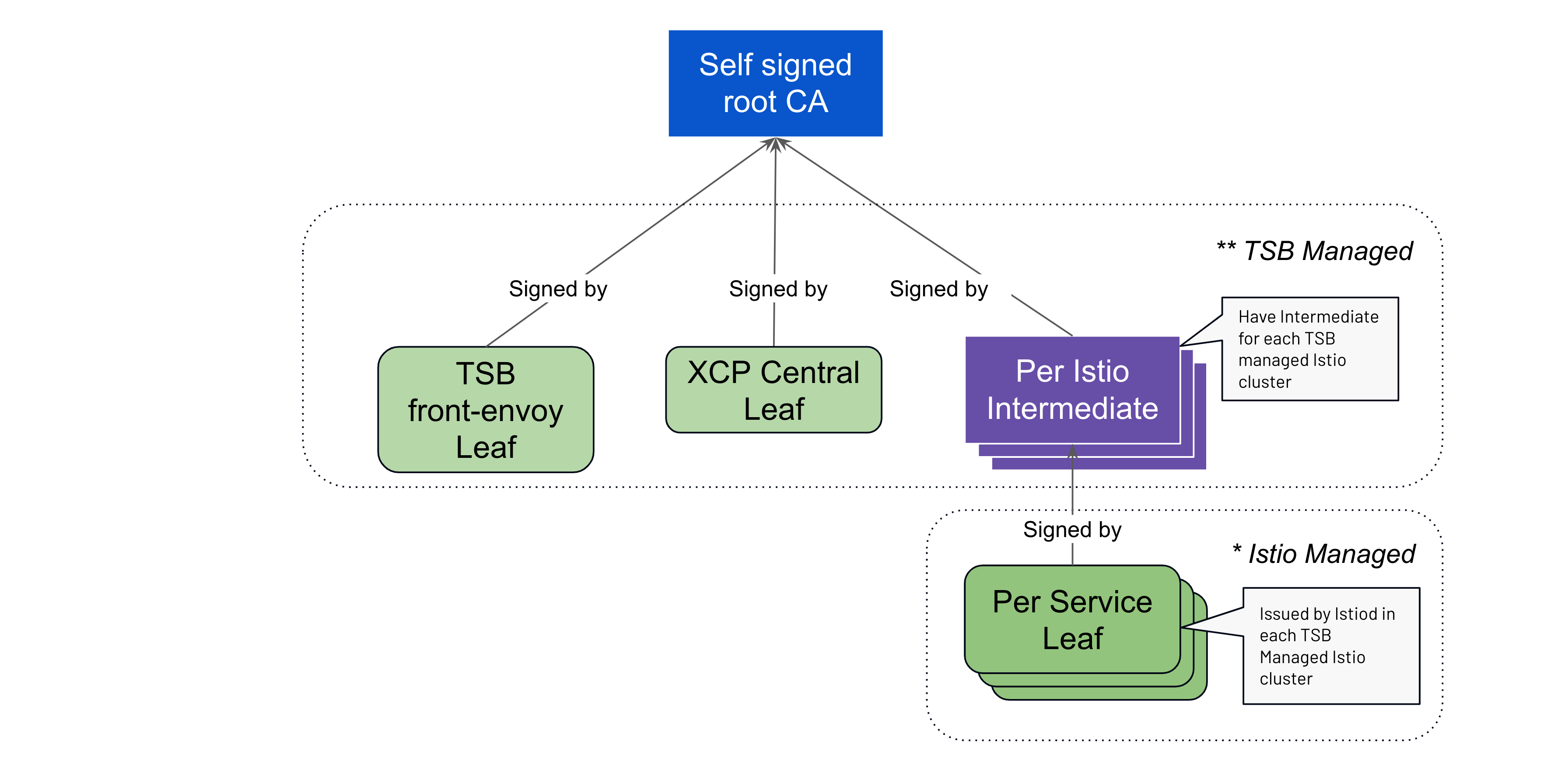
Enable Automated Certificate Management
To enable automated certificate management, you need to set the certIssuer field in the TSB management plane CR or helm values:
spec:
certIssuer:
selfSigned: {}
tsbCerts: {}
clusterIntermediateCAs: {}
The certIssuer field is a map of certificate issuers that you want to enable. Currently, TSB supports the following issuers:
selfSigned: This will provision a self signed root CA that will be used to issue certificates for TSB components.tsbCerts: This will provision TSB TLS certificates for TSB endpoint and also TSB internal certificates.clusterIntermediateCAs: This will provision intermediate CA certificates for application clusters that will be used by Istio in the cluster to issue certificates for application workloads.
To enable automated cluster intermediate CA certificate management, you also need to set following in the TSB control plane CR or helm values:
- Enable
centralProvidedCaCertfield inspec.components.xcptotrue - Enable isolation boundaries by setting env variable
ISTIO_ISOLATION_BOUNDARIESto true for the control plane operator. - Define isolation boundaries by setting
spec.components.xcp.isolationBoundariesfield. See Isolation boundary for more details.
operator:
deployment:
env:
- name: ISTIO_ISOLATION_BOUNDARIES # Enable isolation boundary in the operator
value: "true"
spec:
...
components:
xcp:
...
centralProvidedCaCert: true # Make XCP edge to fetch cluster intermediate CA from management plane
isolationBoundaries: # Define isolation boundaries for the cluster
- name: global
revisions:
- name: default
If you are updating existing TSB control plane to enable automated certificate management for intermediate CA certificates, then you need to restart istiod so it pick up new intermediate CA certificate and then restart istio workloads (sidecars and gateways) to get new workload certificates.
Using External Certificate Management
If you want to use external certificate provisioning, you need to remove the relevant issuer from the certIssuer field in the TSB management plane CR or helm values to avoid conflict. For examples:
- To use existing PKI to provision TSB TLS certificate, remove
tsbCertsfrom thecertIssuerfield. Note that if you disable this, then you also need to need provision TSB internal certificates. - To use existing PKI to provision Intermediate CAs, remove
clusterIntermediateCAsfrom thecertIssuerfield and setcentralProvidedCaCerttofalsein the TSB control plane CR or helm values.
If you plan to use external certificate management for both tsbCerts and clusterIntermediateCAs, then you can remove the certIssuer field from the TSB management plane CR or helm values.