Summary
In these simple exercises, you've seen the beginning of the capabilities of the Tetrate platform to:
- Route and Manage Traffic using Gateways and TrafficSettings
- Enable Zero-Trust architectures with mTLS and SecuritySettings
- Observe traffic and monitor the effect of changes
Understanding the Configuration Hierarchy
Importantly, you've seen a simple use of Tetrate's configuration hierarchy; we've referred to the organization, tenant, workspace and groups:
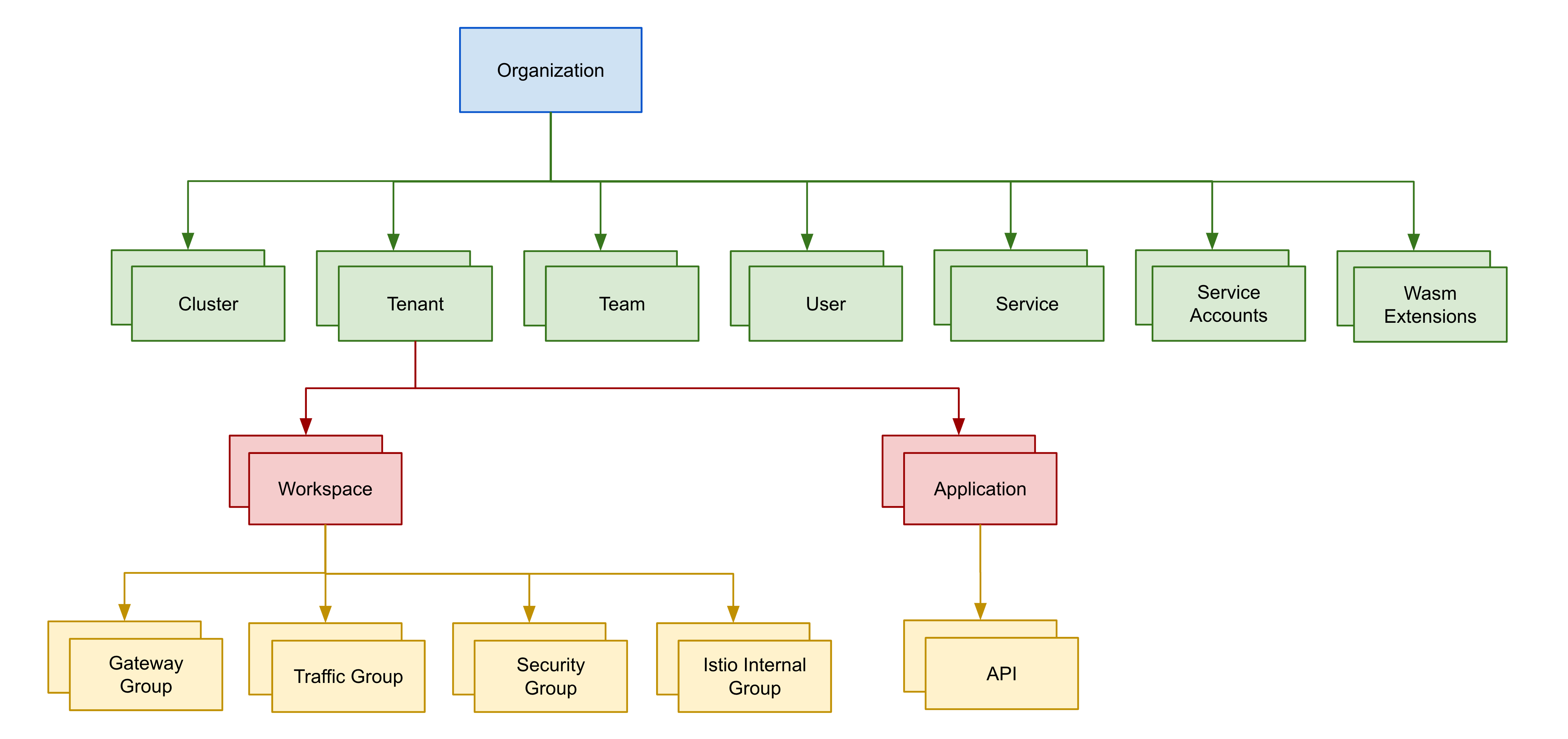
We attached configuration to these resources.
What is next?
These exercises illustrate the Tetrate platform in a very simple environment. The power (and complexity) becomes apparent when you begin to operate at scale:
- Multiple Users: The Tetrate platform uses the hierarchy to support RBAC for multiple users and teams who share the underlying platform
- Multiple Clusters: Configuration is managed centrally be the Tetrate management plane, and applied dynamically depending on the attributes of the managed clusters. The Tetrate platform can manage cross-cluster routing and dynamic failover, and operate tier-1 / tier-2 load balancing to balance the concerns of platform and application teams
- GitOps Configuration: Application owners who deploy applications using GitOps processes can also provide their desired Tetrate platform configuration. The GitOps integration in the platform interoperates with the GitOps source-of-truth to manage application configurations