Expose a TSE-hosted Service to a local Lattice Service Network
Automatically add TSE services to the Lattice Service Registry
Tetrate Service Express (TSE) can automatically add TSE-hosted services to the Lattice Service Registry when services are exposed through an Ingress Gateway. These services can then be discovered and consumed by Lattice clients.
Lattice Integration is currently released as an early preview of the capability. Please provide feedback, but do not rely on this feature in a production environment.
How does the integration work?
The TSE Control Plane on each EKS Workload cluster uses an AWS Controller service to manage Lattice service entries. The AWS Controller component is shipped with TSE and supported by Tetrate. It is not installed by default, and can be added to one or more clusters by redeploying the ControlPlane component.
You connect an EKS Workload cluster to Lattice by associating its VPC with the Lattice Service Network. You then configure that EKS/TSE cluster so that when services are exposed by TSE through an Ingress Gateway, these services are registered with the Lattice Service Network:
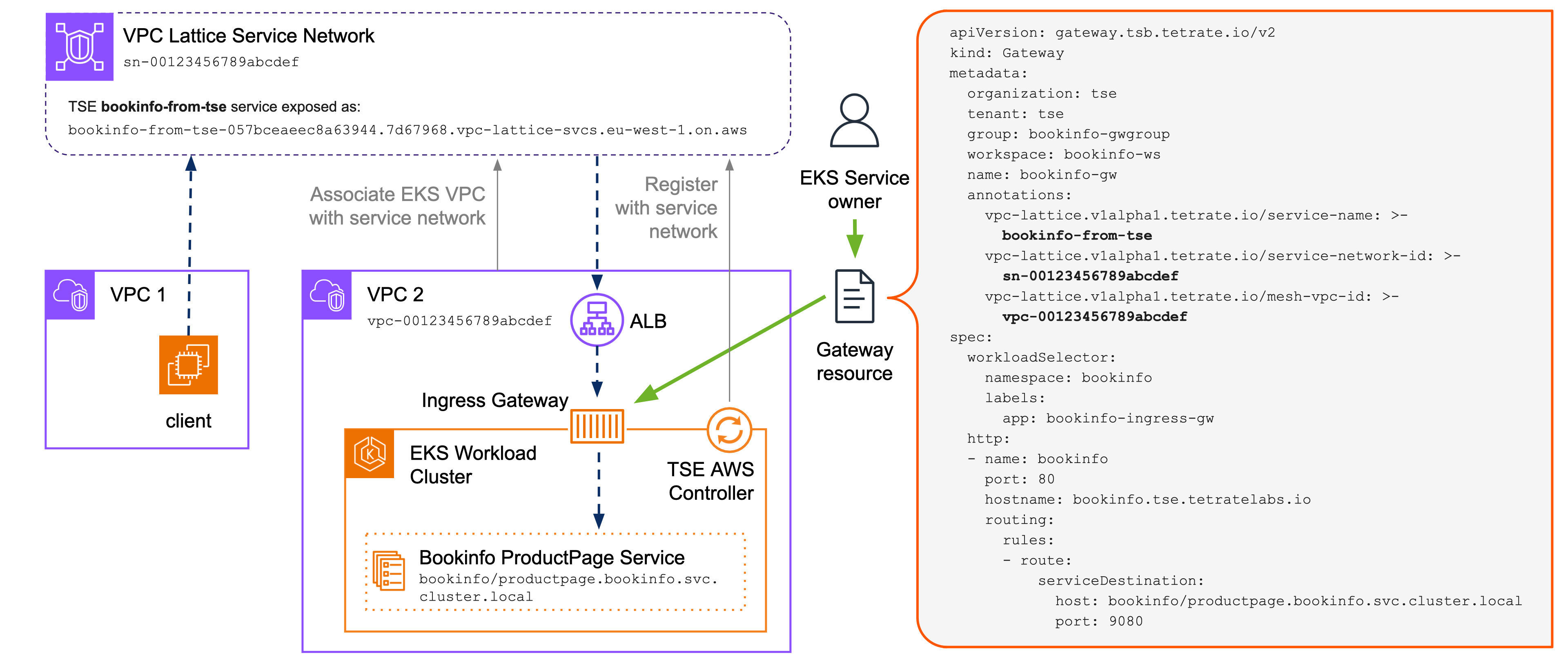 Expose TSE service to Lattice Expose TSE service to Lattice |
|---|
These instructions assume you are familiar with Amazon VPC Lattice and you are familiar with TSE, specifically the process of creating an Ingress Gateway and then exposing a service using a Gateway resource.
The example in these instructions builds on the Getting Started guide to Publish a Service.
Onboard a TSE cluster
Prerequisites
Before you proceed, you should have:
- A Lattice Service Network in your selected region, containing a VPC where there is a simple virtual machine (VM). You will issue curl requests from the VM to access the service in TSE; verify that you can access the VM.
- A TSE EKS Workload cluster in the same region, which you wish to onboard to the Service Network. This cluster should use a different VPC.
Create an IAM Policy
First, create a policy with permissions to manage VPC Lattice resources.
cat <<EOF > AllowVPCLatticeCRUD.yaml
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"vpc-lattice:*",
"elasticloadbalancing:DescribeLoadBalancers",
"ec2:DescribeVpcs"
],
"Resource": ["*"]
}
]
}
EOF
POLICY_NAME=AllowVPCLatticeUpdates
aws iam create-policy --policy-name ${POLICY_NAME} --policy-document file://AllowVPCLatticeCRUD.yaml
Onboard a TSE Cluster
Follow these steps for each TSE EKS Workload cluster you wish to associate with a Lattice Service Network.
Associate with the Lattice Service Network
For each EKS workload cluster, use the AWS Console to create a new VPC association, adding the VPC for the EKS cluster.
Your service network should now contain VPC associations for both the EC2 VM's VPC and the EKS Cluster's VPC.
Create a Service Account
On each workload cluster associated with the Lattice Service Network, create a Service Account for AWS IAM to allow the AWS Controller to manage VPC Lattice resources. The Service Account uses the previously-created policy.
Check that you have correctly set
$EKS_CLUSTER_NAMEand$REGION, and set$ACCOUNTto your 12-digit account ID:SA_NAME=vpclattice-sa
eksctl create iamserviceaccount \
--cluster $EKS_CLUSTER_NAME \
--region $REGION \
--name ${SA_NAME} \
--namespace istio-system \
--attach-policy-arn arn:aws:iam::${ACCOUNT}:policy/${POLICY_NAME} \
--approveEnable the AWS Controller
On each workload cluster associated with the Lattice Service Network, redeploy the Control Plane to enable the AWS Controller service:
helm get values tse-cp -n istio-system > cp-values.yaml helm upgrade tse-cp tse/controlplane \ --namespace istio-system \ --version 1.8.0+tse \ -f cp-values.yaml \ --set spec.providerSettings.lattice.enabled=true \ --set spec.providerSettings.aws.serviceAccountName=${SA_NAME}You can verify the installation and inspect the settings:
kubectl get sa -n istio-system | grep $SA_NAME
kubectl get deployments -n istio-system aws-controller
kubectl get pods -n istio-system -l app=aws-controller
kubectl get clusterrole tsb-aws-controller-cp
kubectl get clusterrolebinding tsb-aws-controller-cpFollow the logs using:
kubectl logs -f -n istio-system -l app=aws-controller
You have now configured your EKS cluster with appropriate permissions and services so that it can publish services on the Lattice Service Network.
Expose a Mesh Service
Prerequisites
Before you proceed, you should have:
- Configured your EKS cluster so it can publish services on the Lattice Service Network.
- Deployed a service, an Ingress Gateway and configured a Gateway Group in your TSE EKS workload cluster.
If you have a complex configuration, you will also need to create appropriate security groups to allow traffic between the VPCs and the Service Network. This is not necessary for the simple, default configuration.
Prepare the Service
The steps in this example use the bookinfo service.
Reference: Preparing the TSE EKS Cluster with the bookinfo application
Deploy the bookinfo application
kubectl create namespace bookinfo
kubectl label namespace bookinfo istio-injection=enabled
kubectl apply -n bookinfo -f https://raw.githubusercontent.com/istio/istio/master/samples/bookinfo/platform/kube/bookinfo.yaml
Create the TSE Workspace
cat <<EOF > bookinfo-ws.yaml
apiversion: api.tsb.tetrate.io/v2
kind: Workspace
metadata:
organization: tse
tenant: tse
name: bookinfo-ws
spec:
displayName: Bookinfo
description: Test Bookinfo application
namespaceSelector:
names:
- "*/bookinfo"
EOF
tctl apply -f bookinfo-ws.yaml
Deploy an Ingress Gateway
cat <<EOF > ingress-gw-install.yaml
apiVersion: install.tetrate.io/v1alpha1
kind: IngressGateway
metadata:
name: bookinfo-ingress-gw
namespace: bookinfo
spec:
kubeSpec:
service:
type: LoadBalancer
EOF
kubectl apply -f ingress-gw-install.yaml
Create a Gateway Group
cat <<EOF > bookinfo-gwgroup.yaml
apiVersion: gateway.tsb.tetrate.io/v2
kind: Group
metadata:
displayName: bookinfo
name: bookinfo-gwgroup
organization: tse
tenant: tse
workspace: bookinfo-ws
spec:
displayName: bookinfo-gwgroup
namespaceSelector:
names:
- "*/bookinfo"
EOF
tctl apply -f bookinfo-gwgroup.yaml
Expose the productpage service with a Gateway Resource
cat <<EOF > bookinfo-ingress.yaml
apiVersion: gateway.tsb.tetrate.io/v2
kind: Gateway
metadata:
organization: tse
tenant: tse
group: bookinfo-gwgroup
workspace: bookinfo-ws
name: bookinfo-gw
spec:
workloadSelector:
namespace: bookinfo
labels:
app: bookinfo-ingress-gw
http:
- name: bookinfo
port: 80
hostname: bookinfo.tse.tetratelabs.io
routing:
rules:
- route:
serviceDestination:
host: bookinfo/productpage.bookinfo.svc.cluster.local
port: 9080
EOF
tctl apply -f bookinfo-ingress.yaml
Verify that the Service can be accessed through the Ingress Gateway
Allow several minutes for AWS to deploy the load balancers to publish the service.
export GATEWAY_IP=$(kubectl -n bookinfo get service bookinfo-ingress-gw -o jsonpath="{.status.loadBalancer.ingress[0]['hostname','ip']}")
curl -s --connect-to bookinfo.tse.tetratelabs.io:80:$GATEWAY_IP \
"http://bookinfo.tse.tetratelabs.io/productpage" | \
grep "<title>"
Expose the Service to Lattice
You need to annotate the Gateway resource that is used to publish the service through an Ingress Gateway:
Obtain the VPC Lattice Service Network ID
The VPC Lattice Service Network ID will look something like sn-00123456789abcdef. You can obtain it from the AWS Console, or using the aws CLI tool with suitable permissions.
SN_NAME=test-vpc
aws vpc-lattice list-service-networks --output json | \
jq --arg name $SN_NAME '.items[] | select(.name==$name) | .id'Troubleshooting: Add permissions to your AWS user
Run
aws vpc-lattice list-service-networks --region ${REGION}. If you get the following error:An error occurred (AccessDeniedException) when calling the ListServiceNetworks operation: User: arn:aws:iam::901234567890:user/YOUR-USER is not authorized to perform: vpc-lattice:ListServiceNetworks on resource: arn:aws:vpc-lattice:REGION:901234567890:servicenetwork/*... you need to enable permissions for that user. For example, you can add the previously-created AllowVPCLatticeUpdates policy to that user's list of permissions policies.
Obtain the cluster VPC ID
The VPC ID for the EKS cluster associated with the Service Network will look something like vpc-00123456789abcdef. You can obtain it from the AWS Console, or using the eksctl CLI tool.
eksctl get cluster $EKS_CLUSTER_NAME --output json | \
jq --arg clusterName $EKS_CLUSTER_NAME '.[] | select(.Name == $clusterName) | .ResourcesVpcConfig.VpcId'Create or Update the Gateway Resource
Annotate your Gateway resource with the Service Network ID, Cluster VPC ID and set the name for the VPC Lattice service.
cat <<EOF > bookinfo-ingress.yaml
apiVersion: gateway.tsb.tetrate.io/v2
kind: Gateway
metadata:
organization: tse
tenant: tse
group: bookinfo-gwgroup
workspace: bookinfo-ws
name: bookinfo-gw
annotations:
vpc-lattice.v1alpha1.tetrate.io/service-name: "bookinfo-from-tse"
vpc-lattice.v1alpha1.tetrate.io/service-network-id: "sn-00123456789abcdef"
vpc-lattice.v1alpha1.tetrate.io/mesh-vpc-id: "vpc-00123456789abcdef"
spec:
workloadSelector:
namespace: bookinfo
labels:
app: bookinfo-ingress-gw
http:
- name: bookinfo
port: 80
hostname: bookinfo.tse.tetratelabs.io
routing:
rules:
- route:
serviceDestination:
host: bookinfo/productpage.bookinfo.svc.cluster.local
port: 9080
EOF
tctl apply -f bookinfo-ingress.yamlDetermine the Lattice-Generated DNS name
Query the Lattice Service Registry for the service you just created (identified by vpc-lattice.v1alpha1.tetrate.io/service-name) and extract the dnsEntry.domainName value:
aws vpc-lattice list-services --output json | \
jq --arg svcName "bookinfo-from-tse" '.items[] | select(.name == $svcName) | .dnsEntry.domainName'You should see something resembling "bookinfo-from-tse-057bceaeec8a63944.7d67968.vpc-lattice-svcs.eu-west-1.on.aws".
Testing the Service
You can now test the integration and service publishing, by attempting to reach the service from another client on the Lattice Service Network. You can use a VM as follows:
curl bookinfo-from-tse-057bceaeec8a63944.7d67968.vpc-lattice-svcs.eu-west-1.on.aws/productpage
Note that it can take 5 minutes or more for the Lattice networking to be configured. You may encounter connection reset by peer or similar errors during this period.
Once configured, you will observe that traffic from a Lattice client is observed to come from an 'External Service':
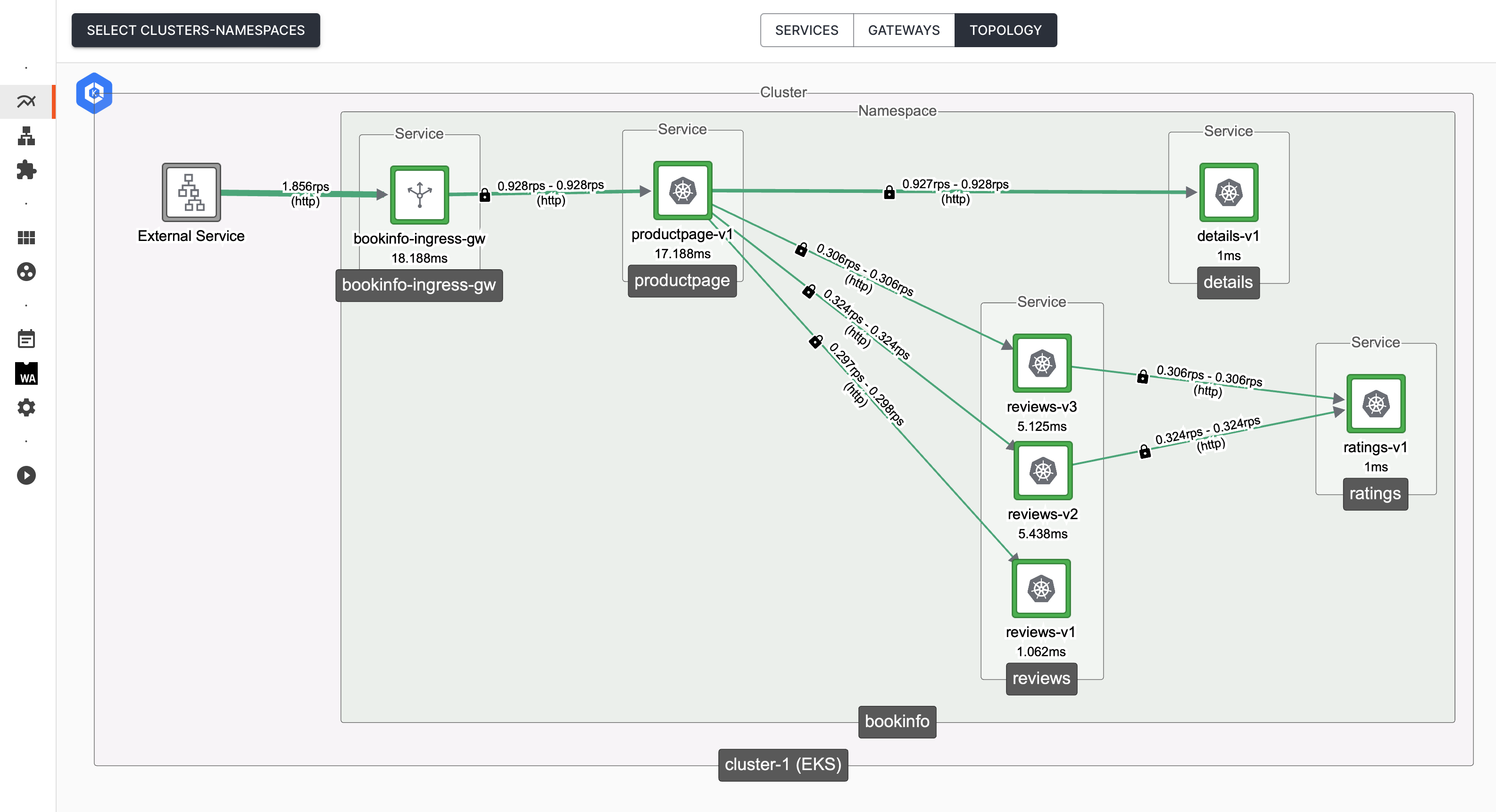 Traffic from a Lattice client is observed to come from an 'External Service' Traffic from a Lattice client is observed to come from an 'External Service' |
|---|